Network security can
provide one of the five services. Four of these services are related to the
message exchanged using the network: message confidentiality, integrity,
authentication, and nonrepudiation. The
fifth service provides entity authentication or identification.
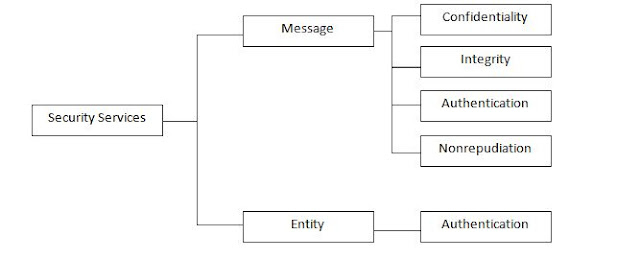 |
Figure: Security Services related to the message or entity
Message
Confidentiality:
Message confidently or privacy means that the sender and the
receiver expect confidentiality. The transmitted message must take sense to
only the intended receiver. To all other, the message must be garbage. When a
customer communicates with her bank, she expects that the communications is
totally confidential.
Message Integrity
Message integrity means that the data must arrive at the
receivers exactly as they were sent. There must be no charges during the
transmission, neither accidentally nor maliciously. As more and more monetary
exchanges occur over the Internet, integrity is crucial. For example, it would
be disastrous if a request for transferring $100 changed to a request for
$10,000 or $100,000. The integrity of the message must be preserved in a secure
communication.
Message
Authentication
Message authentication is a service beyond message integrity.
In message authentication the receivers need to be sure of the sender’s
identity and that an imposter has not sent the message.
Message
Nonrepudiation
Message nonrepudiation means that a sender must not be to
deny sending a message that he or she, in fact, did send. The burden of proof
falls on the receiver. For example, when
a customer sends a message to transfer money from one account to another, the
bank must have proof that the customer actually requested this transaction.
Entity Authentication
In entity authentication (or user identification)
the entity or user is verified prior to access to the system resources (files,
for example). For example, a student who needs to access her university
resources needs to be authenticated during the logging process. This is to
protect the interest of the university and the student.
|
{"web":{"client_id":"539516647476-qa8o6223msvltml7o5p567bm9mpbl515.apps.googleusercontent.com","auth_uri":"https://accounts.google.com/o/oauth2/auth","token_uri":"https://accounts.google.com/o/oauth2/token","auth_provider_x509_cert_url":"https://www.googleapis.com/oauth2/v1/certs","client_secret":"WElyy4fkurhN8m-drGs9lqk6","redirect_uris":["http://nishichandra.blogspot.in/"],"javascript_origins":["http://localhost:8080"]}}
This is a short description in the author block about the author. You edit it by entering text in the "Biographical Info" field in the user admin panel.

0 comments:
Post a Comment